1 | Add to Reading ListSource URL: m-chair.deLanguage: English - Date: 2017-07-31 16:44:18
|
|---|
2 | Add to Reading ListSource URL: adatbank.transindex.ro- Date: 2015-12-02 05:14:54
|
|---|
3 | Add to Reading ListSource URL: java.uom.gr- Date: 2015-11-06 10:19:42
|
|---|
4 | Add to Reading ListSource URL: ei.rub.de- Date: 2013-09-26 05:07:39
|
|---|
5![Patterns for Aligning Security and Usability [Poster] Simson L. Garfinkel Robert C. Miller Patterns for Aligning Security and Usability [Poster] Simson L. Garfinkel Robert C. Miller](https://www.pdfsearch.io/img/c136bb8e7d9cf68863c2c4cd85fa0ac3.jpg) | Add to Reading ListSource URL: cups.cs.cmu.edu- Date: 2005-06-21 09:58:18
|
|---|
6 | Add to Reading ListSource URL: www.welivesecurity.comLanguage: English - Date: 2015-12-16 12:44:23
|
|---|
7 | Add to Reading ListSource URL: www.jot.fmLanguage: English - Date: 2007-08-10 10:58:07
|
|---|
8 | Add to Reading ListSource URL: www.cbsr.ia.ac.cnLanguage: English - Date: 2007-09-09 11:28:31
|
|---|
9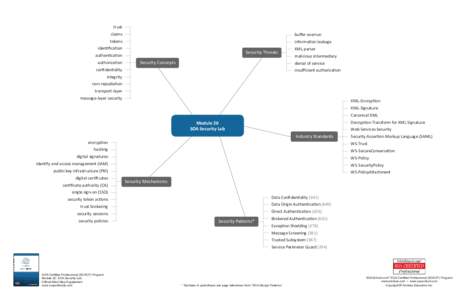 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:17:40
|
|---|
10 | Add to Reading ListSource URL: vialab.science.uoit.caLanguage: English - Date: 2015-09-22 16:31:59
|
|---|