1 | Add to Reading ListSource URL: www.censornet.comLanguage: English - Date: 2017-06-09 09:42:04
|
|---|
2 | Add to Reading ListSource URL: ceur-ws.orgLanguage: English - Date: 2015-08-07 07:25:25
|
|---|
3 | Add to Reading ListSource URL: ceur-ws.orgLanguage: English - Date: 2011-12-19 06:58:36
|
|---|
4 | Add to Reading ListSource URL: ceur-ws.org- Date: 2010-06-24 06:51:12
|
|---|
5 | Add to Reading ListSource URL: ceur-ws.org- Date: 2015-03-12 04:54:52
|
|---|
6 | Add to Reading ListSource URL: biomoby.open-bio.orgLanguage: English - Date: 2007-09-05 19:15:00
|
|---|
7 | Add to Reading ListSource URL: www.ihe.netLanguage: English - Date: 2011-08-19 12:49:37
|
|---|
8 | Add to Reading ListSource URL: hpts.wsLanguage: English - Date: 2013-10-02 05:22:36
|
|---|
9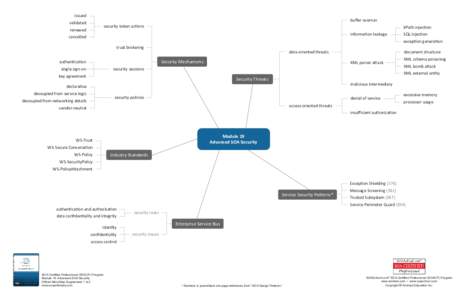 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:18:19
|
|---|
10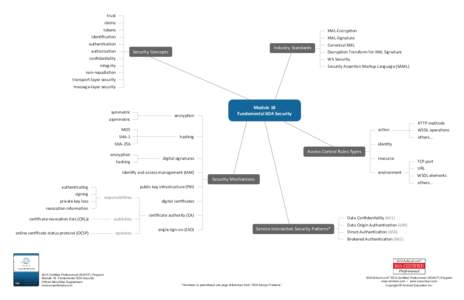 | Add to Reading ListSource URL: www.soaschool.comLanguage: English - Date: 2013-01-08 15:17:27
|
|---|