1 | Add to Reading ListSource URL: static.usenix.orgLanguage: English - Date: 2011-07-08 13:42:23
|
|---|
2 | Add to Reading ListSource URL: www.cs.jhu.eduLanguage: English - Date: 2007-11-09 10:57:13
|
|---|
3 | Add to Reading ListSource URL: www.usenix.orgLanguage: English - Date: 2008-07-14 18:18:35
|
|---|
4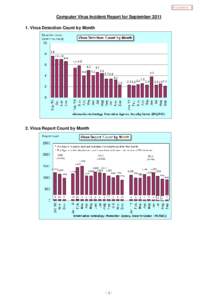 | Add to Reading ListSource URL: www.ipa.go.jpLanguage: English - Date: 2013-05-23 07:51:49
|
|---|
5 | Add to Reading ListSource URL: www.blackhat.comLanguage: English - Date: 2015-05-28 15:51:35
|
|---|
6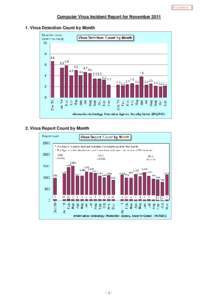 | Add to Reading ListSource URL: www.ipa.go.jpLanguage: English - Date: 2013-05-23 07:51:49
|
|---|
7 | Add to Reading ListSource URL: wdb.ugr.esLanguage: English - Date: 2013-09-30 02:59:52
|
|---|
8 | Add to Reading ListSource URL: jjcweb.jjay.cuny.eduLanguage: English - Date: 2014-12-03 00:00:08
|
|---|
9 | Add to Reading ListSource URL: theory.stanford.eduLanguage: English - Date: 2010-03-09 22:02:42
|
|---|
10 | Add to Reading ListSource URL: jjcweb.jjay.cuny.eduLanguage: English - Date: 2014-12-03 00:02:54
|
|---|