1 | Add to Reading ListSource URL: nob.cs.ucdavis.eduLanguage: English - Date: 2004-10-31 19:48:51
|
|---|
2 | Add to Reading ListSource URL: research.microsoft.comLanguage: English - Date: 1997-12-31 17:54:34
|
|---|
3 | Add to Reading ListSource URL: www.j3l7h.deLanguage: English - Date: 2009-08-23 13:49:42
|
|---|
4 | Add to Reading ListSource URL: disi.unitn.itLanguage: English - Date: 2014-09-10 09:40:14
|
|---|
5 | Add to Reading ListSource URL: www.math.univ-toulouse.frLanguage: English - Date: 2008-04-07 07:55:53
|
|---|
6![Escape From the Matrix: Lessons from a Case-Study in Access-Control Requirements ∗ [Poster Abstract] Escape From the Matrix: Lessons from a Case-Study in Access-Control Requirements ∗ [Poster Abstract]](https://www.pdfsearch.io/img/b93c435b5d1ded9e033bb4f204a1bda1.jpg) | Add to Reading ListSource URL: cups.cs.cmu.eduLanguage: English - Date: 2009-06-16 07:18:28
|
|---|
7![Apollo Education Group Information Security Third Party Information Security Standards Document Type: Standard Document Serial No. [TBD per applicable matrix] Apollo Education Group Information Security Third Party Information Security Standards Document Type: Standard Document Serial No. [TBD per applicable matrix]](https://www.pdfsearch.io/img/3e2abbefed4ef9b58c5b4cd60803afc0.jpg) | Add to Reading ListSource URL: www.apollo.eduLanguage: English - Date: 2016-02-17 20:25:04
|
|---|
8 | Add to Reading ListSource URL: www.scs.stanford.eduLanguage: English - Date: 2010-03-04 18:26:58
|
|---|
9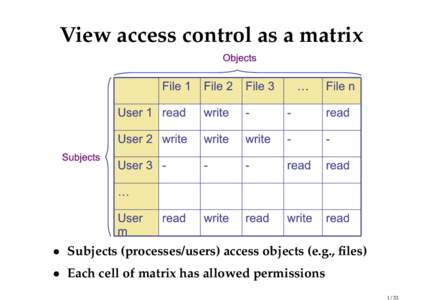 | Add to Reading ListSource URL: www.scs.stanford.eduLanguage: English - Date: 2010-03-04 18:26:58
|
|---|
10 | Add to Reading ListSource URL: swerl.tudelft.nlLanguage: English - Date: 2008-04-25 16:21:05
|
|---|