41 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2013-02-27 15:26:40
|
|---|
42 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2013-02-27 15:26:40
|
|---|
43 | Add to Reading ListSource URL: csrc.nist.govLanguage: English - Date: 2016-07-28 11:33:56
|
|---|
44 | Add to Reading ListSource URL: wiki.umiacs.umd.eduLanguage: English - Date: 2009-05-12 14:48:13
|
|---|
45 | Add to Reading ListSource URL: www.spyrus.comLanguage: English - Date: 2015-08-05 12:42:41
|
|---|
46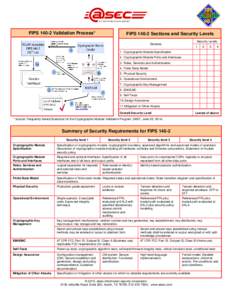 | Add to Reading ListSource URL: www.atsec.comLanguage: English - Date: 2015-12-09 15:15:24
|
|---|
47 | Add to Reading ListSource URL: events.iaik.tugraz.atLanguage: English - Date: 2008-07-21 05:29:13
|
|---|
48 | Add to Reading ListSource URL: www.pdl.cmu.eduLanguage: English - Date: 2015-09-03 13:39:36
|
|---|
49 | Add to Reading ListSource URL: roads.maryland.govLanguage: English - Date: 2016-04-12 16:00:39
|
|---|
50 | Add to Reading ListSource URL: webdocs.cs.ualberta.caLanguage: English - Date: 2009-10-06 18:16:29
|
|---|