31 | Add to Reading ListSource URL: opensecuritytraining.infoLanguage: English - Date: 2015-10-14 22:08:48
|
|---|
32 | Add to Reading ListSource URL: www.sentinelone.comLanguage: English - Date: 2016-05-23 01:13:39
|
|---|
33 | Add to Reading ListSource URL: www.testeznous.luLanguage: English - Date: 2016-04-14 08:33:53
|
|---|
34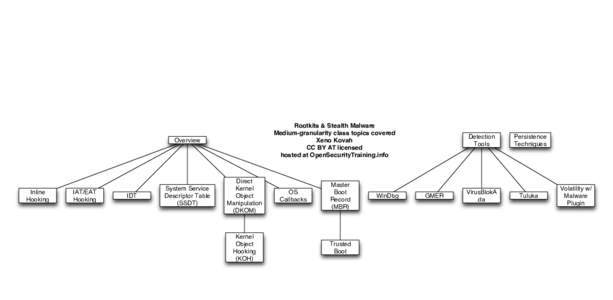 | Add to Reading ListSource URL: www.opensecuritytraining.infoLanguage: English - Date: 2014-03-02 22:01:32
|
|---|
35 | Add to Reading ListSource URL: www.opensecuritytraining.infoLanguage: English - Date: 2014-03-02 22:01:43
|
|---|
36 | Add to Reading ListSource URL: www.opensecuritytraining.infoLanguage: English - Date: 2014-03-02 22:01:46
|
|---|
37 | Add to Reading ListSource URL: www.trailofbits.comLanguage: English - Date: 2016-04-15 11:36:17
|
|---|
38 | Add to Reading ListSource URL: www.imf-conference.orgLanguage: English - Date: 2014-05-21 12:58:37
|
|---|
39 | Add to Reading ListSource URL: www.trailofbits.comLanguage: English |
|---|
40 | Add to Reading ListSource URL: www.citesandinsights.infoLanguage: English - Date: 2006-07-15 15:59:31
|
|---|