91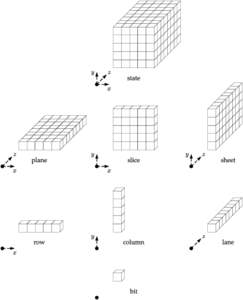 | Add to Reading ListSource URL: keccak.noekeon.org- Date: 2013-02-27 15:26:40
|
|---|
92 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2014-04-18 11:02:15
|
|---|
93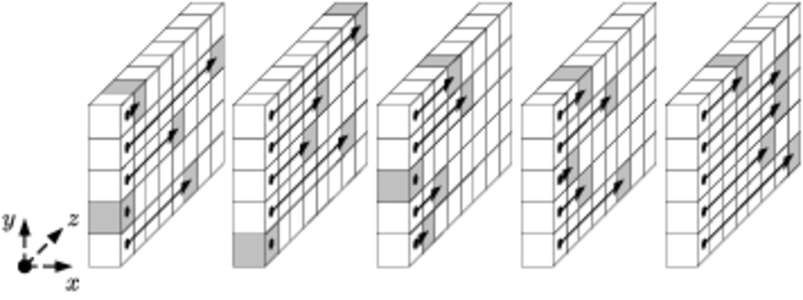 | Add to Reading ListSource URL: keccak.noekeon.org- Date: 2013-02-27 15:26:40
|
|---|
94 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2013-02-27 15:26:40
|
|---|
95 | Add to Reading ListSource URL: sponge.noekeon.orgLanguage: English - Date: 2013-02-27 15:27:45
|
|---|
96 | Add to Reading ListSource URL: sponge.noekeon.orgLanguage: English - Date: 2013-02-27 15:27:45
|
|---|
97 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2013-02-27 15:26:40
|
|---|
98 | Add to Reading ListSource URL: keccak.noekeon.orgLanguage: English - Date: 2013-02-27 15:26:40
|
|---|







