1 | Add to Reading ListSource URL: www.ieee-security.orgLanguage: English - Date: 2017-04-03 16:01:55
|
|---|
2 | Add to Reading ListSource URL: www.ieee-security.orgLanguage: English - Date: 2017-05-11 01:15:34
|
|---|
3 | Add to Reading ListSource URL: assets.morpheusdata.comLanguage: English - Date: 2016-02-13 13:58:58
|
|---|
4 | Add to Reading ListSource URL: app.etapestry.comLanguage: English - Date: 2014-08-14 11:37:45
|
|---|
5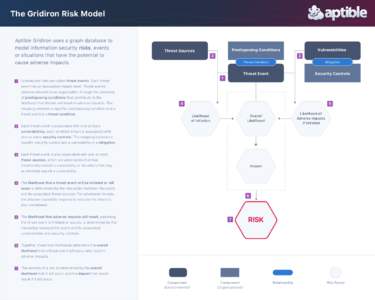 | Add to Reading ListSource URL: www.aptible.com- Date: 2018-03-21 14:07:12
|
|---|
6 | Add to Reading ListSource URL: adatbank.transindex.ro- Date: 2015-12-02 05:14:54
|
|---|
7 | Add to Reading ListSource URL: www.nebraskacert.org- Date: 2016-01-21 01:41:50
|
|---|
8 | Add to Reading ListSource URL: nosql2015.dataversity.net- Date: 2015-07-30 13:13:30
|
|---|
9 | Add to Reading ListSource URL: mapcontext.comLanguage: English - Date: 2008-08-29 23:31:17
|
|---|
10 | Add to Reading ListSource URL: www.a-sit.atLanguage: English - Date: 2010-04-14 10:56:00
|
|---|